Strange Admin Panel Bypass Story | | Bug Bounty
Hello Friends, My name is Ranjeet Singh and currently I am pursuing B-Tech from LPU and a part time bug hunter. I am doing bug hunting from past 3 years & I am still noob so if I will do some mistake then please notify me so I can correct it. So without wasting time lets get into the point.

One of my friend has given this private site so lets call that domain as :<redacted>.com
So the target has vast scope i.e *.redacted.com . So I started recon. because without recon we don’t get to know how things are working , developers mindset and lots of interesting subdomains etc.
This is the steps how I recon. Basically I use my own private tool for recon but I am going to explain how I have created this tool using some public tools.If you know bash scripting then you can easily create your own tool using this methodology.
My recon starts with like first I gather subdomain using Amass, Asstefinder then send subdomains to httprobe for checking which is alive and then I check for open ports using nmap then at last I take screenshot using eyewitness.
So after recon I start with checking screenshot that we have taken during recon process. So I have discovered lots of admin panel but I don’t know weather I was able to bypass or not so on 1 day I have checked main app. and checked each functionalities + endpoints of that app but I haven’t found anything interesting. Then on 2 day I was like lets try some sqli payloads on admin panel but here too I haven’t found any sqli.
Then I started visiting each admin panel & checking js files in hope that I will found something interesting .But again I haven’t found anything interesting.
So one by one I have picked each subdomain and see how it looks like when I have first visited to this subdomain.redacted.com . It was asking for username and password for login.
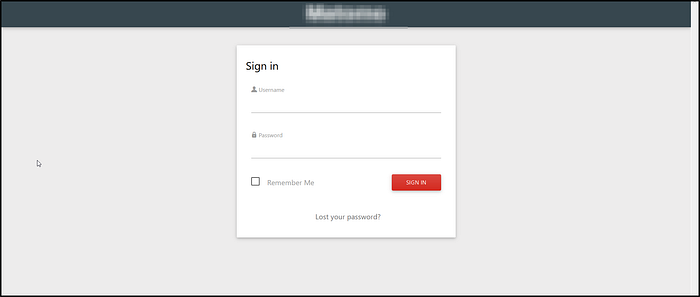
So I started fuzzing for directories,any js files and I have found one endpoint and that endpoint has redirected me to another endpoint and the interface was like this :)

I was like w00woo !! because this is the first time I have found something like this from past 3 years.
After that I have used google, github search and from every where I have collected ton’s of emails of that ‘@redacted.com’ . And again started brute forcing email parameter and approx 3–5 has shown 2xx response and other has shown 4xx response. So I have tried to login using that 2xx response email addresses and ya I was into the admin panel :) Then I have reported this and after 4–5 days they have patched and rewarded me with $$$$ 😎
At last I want to say few things :
Everything depends on observation and it was not like if you are not finding p1-p2 then you are not good.Everyone is good at his own level.So instead of demotivating keep trying until you find something interesting.May be sometime you report will get dup. but still try to find something more interesting that older one.
Hope you have enjoyed this :)
Stay Safe & Happy !!
Thank You
